Washington, DC - This is the last week for website owners using Symantec SSL certificates issued before December 1, 2017 to replace their certificate. Failing to do so will result in your website breaking. Next week Google will roll out Chrome 70, which will distrust all remaining Symantec CA brand SSL certificates. This is only for websites using SSL certificates issued off Symantec’s roots. If you have re-issued or replaced your SSL certificate after December 1, 2017 this does not apply to you.
If it feels like we’ve covered this topic before—we have. Extensively. But this morning when I got to my office my boss wheeled in a large cart with a sheet draped over it and said, “I need you to beat this dead horse.”
So, beat it I will. Here’s a rundown of what’s happening, how we got here and what you need to do if this change impacts you.
Let’s hash it out…
Why do Symantec SSL Certificates Need to be Replaced?
Sit back and let me tell you the tale of a Certificate Authority and a browser and how two companies nearly broke the internet. Ok, that might be a bit grandiose—but you try writing about this for the 15thtime and see how creative you get.
Back in 2015 Symantec ran afoul of Google for the first time after issuing some bad test certificates. We tend to downplay the severity of this first mistake, but it was pretty major. Google found that Symantec had been issuing unauthorized SSL certificates domains owned by Google, Opera and three other organizations. The scandal caused Symantec to fire a number of employees and Google required Symantec to begin adding all the certificates it issued to Certificate Transparency logs. At that point in time only EV certificates were required to be logged.
A year later, Symantec got in trouble for mis-issuing a new batch of test certificates. While Symantec claimed it was just 33 certificates Google estimated it was more like 30,000. When Google investigated further it unearthed lax oversight over validation in some regions, too.
In college sports, the worst allegation that the NCAA (US college sports’ governing body) can level at a program is a loss of institutional control. That’s basically what Google alleged after the second set of mis-issuances in 2016.
Now, this is where the opinion tends to split. From the browsers’ perspective (not just Google, but Mozilla, Apple and Microsoft, too) these mistakes undermined faith in Symantec’s entire PKI. How could any Symantec SSL certificate be trusted knowing that there was such lax oversight over the validation required for issuance. By that logic, Symantec had to be distrusted.
The other camp, which was largely consistent of the commercial CA industry, didn’t have a problem so much with the distrust as with the potential impact to customers and end users. The average site owner doesn’t pay any attention to the goings on of the digital certificate industry. And Symantec is one of the few brands with crossover brand recognition owing to its highly-popular Norton Antivirus product. Outside of the SSL/TLS industry Symantec enjoys a sterling reputation, that’s part of what’s buoyed its market share.
Customers shouldn’t be punished for choosing Symantec, especially given that they didn’t have any idea about these issues in the first place. And even though Google attempted to give extended timelines for replacement, that’s still effectively what happened—Symantec’s customers were punished.
DigiCert Saves the Day
The original plan between Google and Symantec called for issuance to be passed on to a managed CA until Symantec could rebuild its own PKI. However, that was never really a tenable solution. Fortunately, DigiCert stepped in and purchased the Symantec CA in the Fall of 2017.
In the long run, that’s probably the best thing that could have happened.
It’s still worth pointing out what an undertaking this was though. DigiCert didn’t just purchase the rights to trademarks and brands, it acquired talent and infrastructure, too. Then it had to scramble to integrate new personnel, integrate various processes and systems and scale up all aspects of its operation – support, account management, sales – to incorporate Symantec’s customer-base with its own.
And all of this needed to be finished up by the beginning of December so that it could start re-issuing millions (literally, millions) of certificates before Google’s deadlines.
That’s a near Herculean effort, and aside from one or two cases – outliers – the internet hasn’t broken.
So, hats off to DigiCert.
What Symantec CA Brand SSL certificates are going to be distrusted?
Ok, so let’s get down to brass tacks. The final Google-Symantec distrust doesn’t just affect Symantec SSL certificates, it also affects the Symantec subsidiary brands, too.
- Symantec
- GeoTrust
- Thawte
- RapidSSL
This is the final distrust, so any SSL certificates issued off any of those CAs’ roots will break. Here’s the best way to figure out if this will affect you: Was your SSL certificate issued after December 1, 2017?
Since December, DigiCert has been issuing for Symantec and its subsidiaries off its own roots (the DigiCert roots). So, as long as your Symantec CA brand SSL certificate was issued or re-issued after December 1, 2017, you’re in the clear.
Here’s how to check: regardless of what browser you’re using, click on the padlock icon in the address bar of your browser and navigate to the certificate details. Now, check the Begins On date:
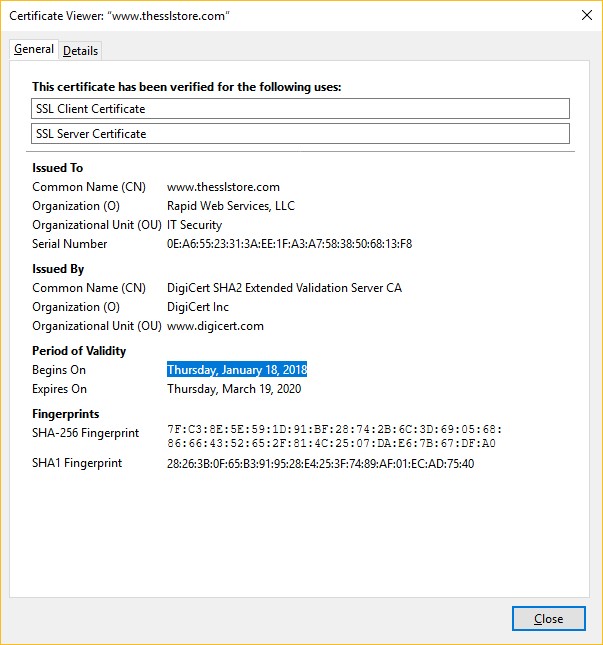
Or, if you want, we have a tool that can check for you.
If you’re using a Symantec CA brand SSL certificate issued before December 1, 2017 and you haven’t re-issued or replaced it yet, you have about a week before your website breaks.
What happens when an SSL certificate is distrusted?
This is tough to explain without at least a basic working knowledge of Public Key Infrastructure. Every computer system keeps a Root Store. This store contains a set of trusted Root CA Certificates. When a CA issues an SSL certificate, it signs it with one of its private keys. If that digital signature can be traced back to one of the roots in the system’s trust store, the system will trust the certificate.
What Google and the other browsers have done to distrust Symantec CA brands is remove their roots from the various Root programs, and thus the root stores. Now when a client is presented with an SSL certificate that should chain back to one of the removed Symantec CA brand roots, it won’t be able to trace it back to one of the roots in its trust store and will issue a browser warning about the site.
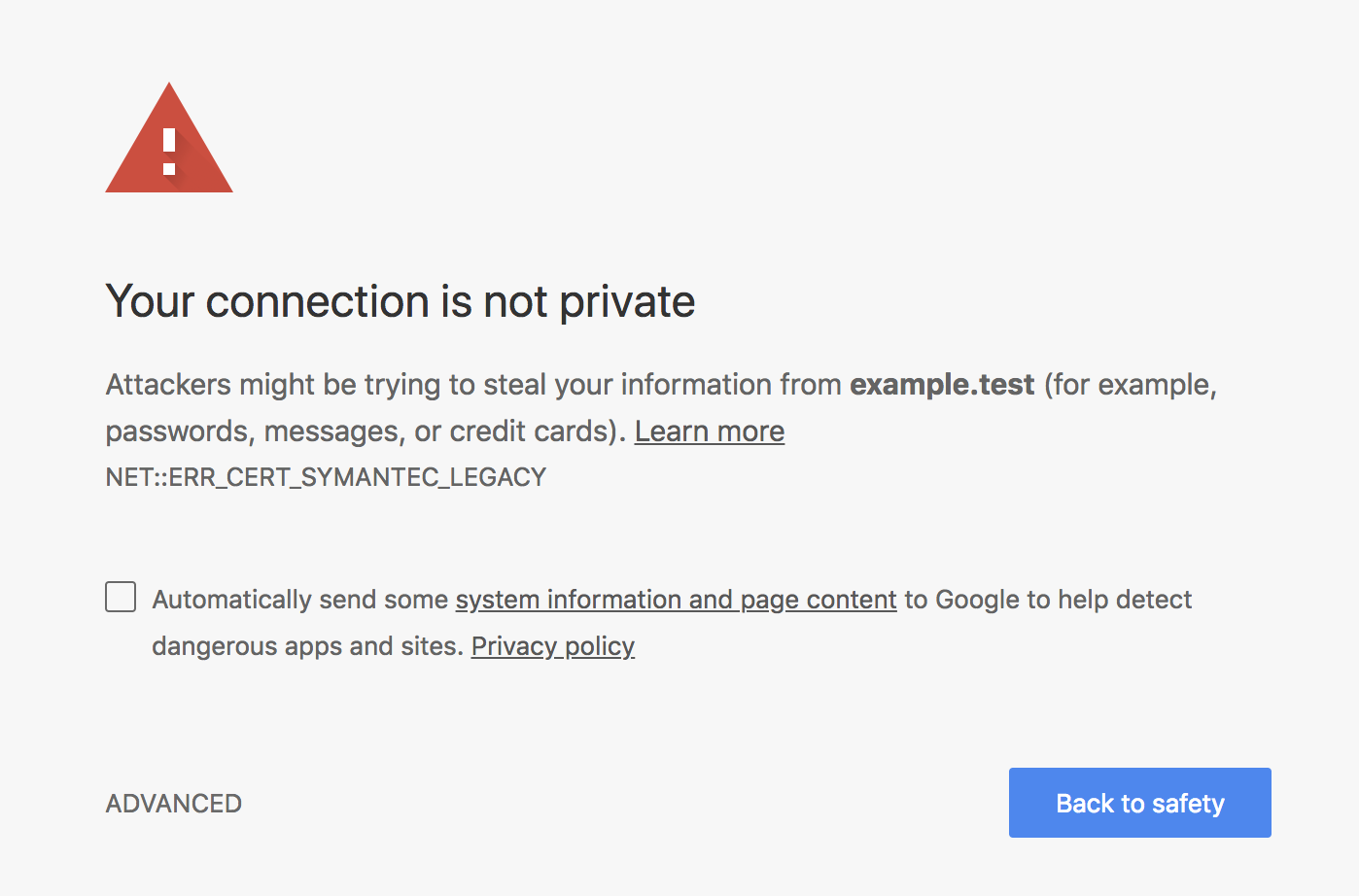
One of the biggest misnomers throughout all of this deals with Google’s root program. The obvious assumption is that Google Chrome would use the Google root program, but that’s not the case. While Mozilla’s Firefox browser relies on the Mozilla root program, Google Chrome actually uses the root store that is present on whatever operating system it’s running on (Apple, Microsoft, etc.). The Google root program is for the Android OS.
So how can Google distrust a root in Chrome before the root programs distrust it? Blacklists. Google filters roots against its own blacklist, which allows it to distrust roots without running its own root program for Chrome.
What do I need to do if my SSL certificate is going to be distrusted?
Don’t panic. There’s still about a week before Google rolls out Chrome 70. But you do need to act now, Chrome is the most used browser in the world, with well over 50% market share.
If your website is using an affected SSL certificate, you have a couple of options:
- You can contact us. I typically try to avoid being openly sales-y in this space, but we have been in the SSL/TLS business for over a decade and we’ve built out the infrastructure to help you quickly re-issue or replace your Symantec CA brand SSL certificate(s).
- Contact DigiCert. While we’re platinum elite partners with DigiCert and can handle your needs for you, you can also go directly to DigiCert for re-issuance/replacement.
And given the fact that many of these SSL certificates will need to be renewed within a few months of re-issuance, DigiCert has also extended the window for renewals. Now site owners can renew and carry up to seven months over to their new certificate. This should help reduce administrative burdens considerably.
And one last thing, the Symantec CA brands are trustworthy once again now that they are being run by DigiCert. All Symantec CA brand SSL certificates – Symantec, GeoTrust, Thawte & RapidSSL – chain back to the DigiCert trusted roots as of December 1, 2017.
So, one last time: this is your final chance to replace any original Symantec CA brand SSL certificates issued before December 1, 2017 before your website breaks. Don’t wait on this.